Summary
Biometric authentication is powerful, but irreversible when compromised. This guide explains how enterprises can deploy biometrics safely using a risk-based, privacy-first identity management strategy that balances security, cost, and user trust.
The Security Paradox Enterprises Face Today
Your fingerprint never changes. Neither does your Iris pattern or facial geometry. Their permanence is the foundation for biometric authentication. However, its biggest strength can become the weakest link and potentially catastrophic, if compromised. Unlike a password, you can reset in minutes, a biometric information is irreversible.
This paradox keeps enterprise decision-makers across the globe awake at night. While biometric systems promise to eliminate password vulnerabilities, they introduce new challenges: substantial upfront costs for implementing systems capable of handling biometric information, privacy concerns around collecting & handling personal data, and technical limitations such as false positives and algorithmic biases.
Recent employee biometric data collection cases have sparked debates around consent and potential misuse. Surveys reveal this tension clearly. Organizations recognize that biometrics significantly cut identity fraud and is essential in several contexts, yet many remain wary of breaches. Users demand proof of responsible data handling from data collection to data deletion, and with user consent.
In the above context, these questions have become more urgent to the decision makers – the C-Suite personnel:
- How do you harness biometric security without exposing your organization to irreversible data breaches?
- How do you justify the investment on biometric information security?
This blog attempts to answer these questions, more importantly on why it is essential for enterprises to have a robust biometric based authentication system.
The Multi-Layered Authentication Strategy
Implementing the biometrics-based authentication, as a default setup replacing the traditional authentication method is not a practical approach. Authentications in enterprise applications should combine biometrics with traditional credentials in a risk-adaptive framework, i.e. biometric authentication should be deployed strategically where it matters most while using lower-friction methods for routine access.
This approach delivers three critical advantages. First, it reduces reliance on any single factor of authentication, so a compromised biometric attribute (such as face, fingerprint, iris) doesn’t become catastrophic. Second, it justifies costs efficiently by reserving expensive biometric infrastructure for high-risk scenarios. Third, it improves user acceptance by matching authentication rigor to actual threat levels.
Privacy-by-design approach
Principles form the foundation of any system. A principal on Data Privacy, especially of biometric data, should not be an after-thought. Applications that handle biometric data should encrypt biometric templates in transit and at rest, store them in decentralized formats where possible, and use template protection schemes where stored data cannot be reverse engineered. When in doubt, build pilot programs to build confidence while containing risk. Start with executive access or high-value transactions and expand based on results.
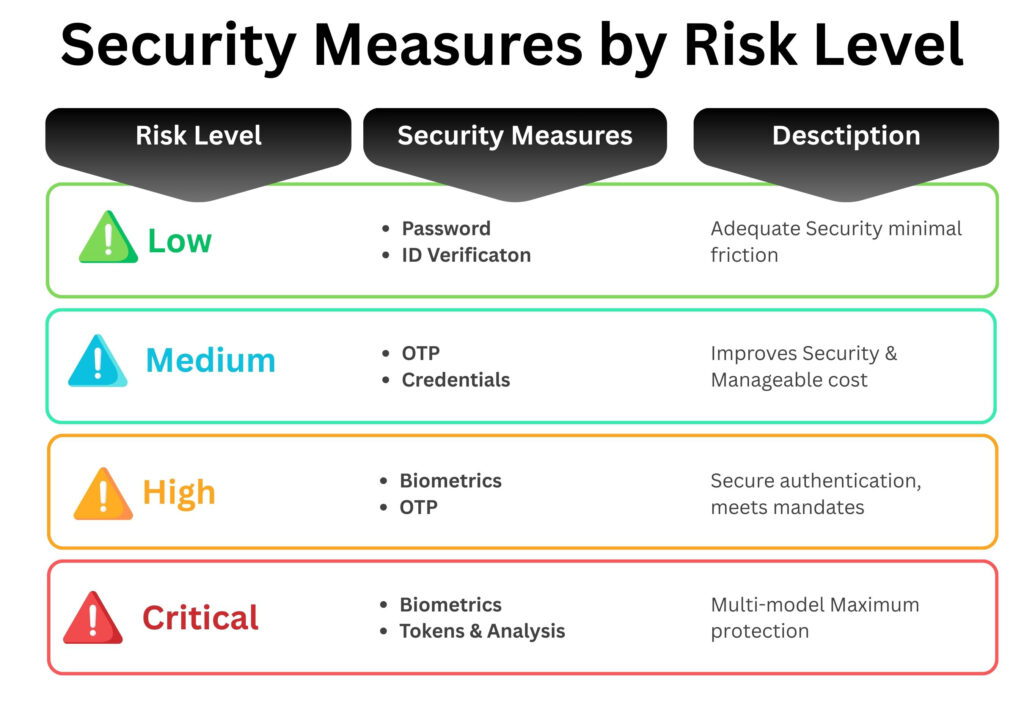
A Decision Framework for Risk-Based Authentication
Match security measures to actual risk levels, stepping up authentication mechanisms from low-friction methods to robust biometric verification for high-stakes scenarios.
Low-Risk Scenarios (routine activities from trusted devices) need only passwords/ PINs – adequate security with minimal friction and cost. For added convenience without compromising security, mobile device level complement password/PIN entry, eliminating the need for biometrics to be stored or processed at the bank’s end.
Medium-Risk Scenarios (new devices, unusual times, moderate-value transactions) warrant one-time passwords via SMS or passkeys combined with credentials. Authenticator apps generate time-based codes locally without relying on cellular networks, eliminating SIM-swap vulnerabilities that plague SMS-based OTP.
High-Risk Scenarios (number of transactions or transaction value exceeding a pre-defined limit, international transfers, post-fraud alerts) demand biometrics combined with OTP. Passkeys, leveraging device-based public key cryptography, offer even stronger protection by binding authentication to the specific device while keeping biometric data local. This adds brief verification steps, while keeping the cost manageable and improving security substantially. Banks implementing this for mobile payments report more secure authentications while meeting Open Banking Frameworks and strong authentication mandates.
Critical Scenarios (executive access, trading operations, disputed transactions) require biometrics alongside hardware tokens (such as YubiKeys or RSA SecurID) and behavioural analysis – higher friction justified by maximum protection against sophisticated attacks. Liveness checks and deep-fake identifications are included in the checks along with cryptographic keys generated by hardware tokens. The keys are impossible to intercept or duplicate remotely and live-ness checks cannot be surpassed with deep-fakes.
Understanding the Trade-offs in various authentication mechanisms
Passwords have always been the default authentication mechanism. But they can be shared or forgotten. An additional trust is added with a two-factor authentication, more commonly a time-based one-time-password (OTP). OTP authentication adds 10-30 seconds, as a friction to the end customer, but avoids privacy concerns.
Passkeys (FIDO/WebAuthn) is another newer and more secure technology. This passwordless authentication technology uses cryptographic key pairs stored on user devices. Biometrics (fingerprint, face) or PINs to are used to unlock a private key, one of the key pairs) stored the user’s device, which is verified with a public key, the other one stored on the server. This method enables faster, easier sign-ins across devices, websites, and apps without transferring any biometric data.
Multi-Factor Authenticator (MFA) solution providers like TrueID make the passkeys resistant to phishing by creating unique key pairs on the device, with the service storing the public key and the app securing the private key for biometric/PIN-verified challenges.
Biometric authentication offers seamless mobile verification but fails in edge cases like poor lighting or injuries, resulting in 1-5% error rates requiring fallback mechanisms.
The approach for implementing the multi-factor authentication depends not only on user experience and threat detection but also costs. Per authentication cost with OTP is much less when compared with per user initial setup for biometrics, but organizations replacing OTP with biometrics for high-risk transactions report significant fraud reduction that justifies higher upfront costs. For example, on HSBC’s mobile application, biometric verification (facial recognition) for high-risk transactions enhanced fraud prevention, boosting mobile banking adoption rate from 60% to 85%.
The Path Forward
The biometric dilemma isn’t whether to adopt biometric authentication—it’s how to deploy it intelligently within a comprehensive identity management strategy. Successful implementations require robust privacy protections from the ground up, selecting authentication methods based on actual risk rather than perceived sophistication, and partnering with experts who understand both technical complexities and regulatory landscapes across the boundaries.
Identity breaches damage customer trust, invite regulatory penalties, and can cripple operations. But with careful planning, risk-based implementation, and the right expertise, enterprises can harness biometric technology’s security benefits while managing its inherent challenges. Your organization’s identity management strategy should evolve with the threat landscape—the question is how to incorporate biometrics in ways that protect your organization, respect user privacy, and maintain operational efficiency.
Ready to develop a risk-based authentication strategy tailored to your organization? Our team brings deep expertise in biometric identity management, regional compliance requirements, and enterprise IAM integration across the Middle East.




